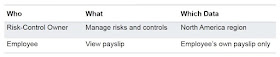
- WHO is the User
- WHAT actions the user can perform, reflected in job and duty roles
- WHICH set of data is reflected in data security policies
An example is below:
Security Processes
For more full-detailed Tutorials and Tips, check out #TheOracleProdigy at https://lifeofanoracleprodigy.blogspot.com/
Follow The Oracle Prodigy on Facebook (https://www.facebook.com/theOracleProdigy/) and Twitter (https://twitter.com/D_OracleProdigy)


No comments:
Post a Comment